Examining the Vulnerabilities: A Deep Dive into Network Ports and Their Susceptibility to Exploitation
NETWORK SECURITY


Introduction
In today's interconnected world, network security is of paramount importance. As organizations rely more and more on computer networks to store and transmit sensitive information, it becomes crucial to understand the vulnerabilities that exist within these networks. One area that often goes overlooked is the security of network ports. In this article, we will take a deep dive into network ports and explore their susceptibility to exploitation.
Understanding Network Ports
Network ports are virtual endpoints that allow computers to communicate with each other over a network. They serve as a gateway for data to enter or exit a computer system. Each network port is assigned a unique number, known as a port number, which helps identify the specific service or application that is using it.
There are two types of network ports: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). TCP ports are connection-oriented, meaning they establish a reliable and ordered communication channel between two devices. UDP ports, on the other hand, are connectionless and provide a faster but less reliable form of communication.
The Role of Network Ports in Exploitation
Network ports play a crucial role in the exploitation of computer systems. Hackers often target open ports as potential entry points to gain unauthorized access to a network. By identifying vulnerable ports, attackers can exploit weaknesses in the associated services or applications to launch various types of attacks, such as denial-of-service (DoS) attacks, remote code execution, or data breaches.
One common method used by hackers is port scanning. Port scanning involves systematically scanning a range of IP addresses for open ports. Once an open port is discovered, the attacker can then proceed to exploit any vulnerabilities associated with that port.
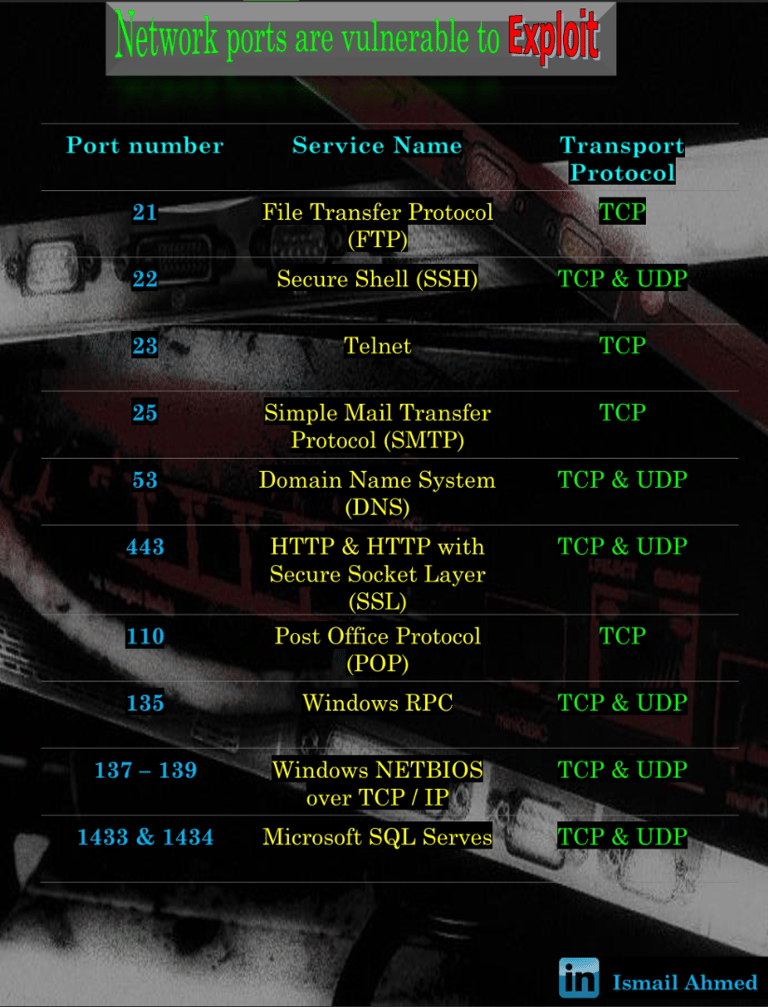
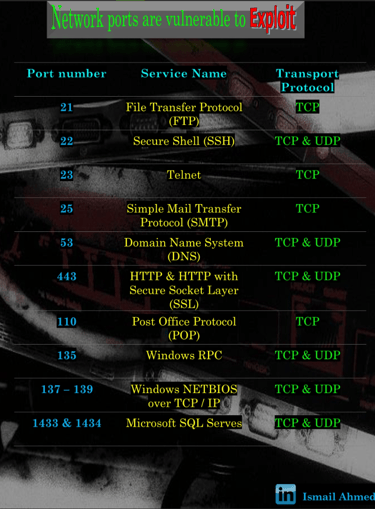
The 13 most vulnerable ports to check when pentesting
Network ports can be vulnerable to a variety of attacks. Some common vulnerabilities include:
1. Default or Weak Credentials
Many services or applications use default usernames and passwords, which are often well-known and easily exploitable. Additionally, weak or easily guessable passwords can also leave network ports vulnerable to brute-force attacks.
2. Outdated or Unpatched Software
Software vulnerabilities are regularly discovered and patched by developers. However, if organizations fail to update their software or apply patches in a timely manner, network ports running outdated versions can become easy targets for exploitation.
3. Misconfigured Firewall Rules
A misconfigured firewall can inadvertently leave network ports exposed. If firewall rules are not properly set up to restrict access to specific ports, attackers can exploit this oversight to gain unauthorized access.
4. Lack of Encryption
Unencrypted network traffic can be intercepted and manipulated by attackers. Network ports that transmit sensitive information without encryption are at a higher risk of data breaches and unauthorized access.
5. Buffer Overflow Vulnerabilities
Buffer overflow vulnerabilities occur when an application or service does not properly validate the size of incoming data. Attackers can exploit this vulnerability by sending excessive data to a network port, causing a buffer overflow and potentially executing arbitrary code.
Preventing Network Port Exploitation
Protecting network ports from exploitation requires a proactive approach to network security. Here are some best practices to consider:
1. Regularly Update Software
Ensure that all software and applications running on network ports are kept up to date with the latest security patches. Implement a patch management process to ensure timely updates.
2. Use Strong Authentication
Enforce the use of strong and unique passwords for all services and applications. Consider implementing multi-factor authentication for an added layer of security.
3. Implement Firewalls and Intrusion Detection Systems
Configure firewalls to restrict access to only necessary ports and protocols. Intrusion detection systems can help identify and alert you to any suspicious activity on your network ports.
4. Encrypt Network Traffic
Enable encryption for all sensitive data transmitted over network ports. This can be achieved through the use of secure protocols such as SSL/TLS.
5. Regularly Conduct Vulnerability Assessments
Perform regular vulnerability assessments and penetration testing to identify and address any weaknesses in your network ports. This will help you stay one step ahead of potential attackers.
Conclusion
Network ports are an essential component of computer networks, but they can also be a significant vulnerability if not properly secured. Understanding the vulnerabilities associated with network ports is crucial for organizations to protect their systems from exploitation. By following best practices and implementing robust security measures, organizations can minimize the risk of network port attacks and safeguard their valuable data.